Hunting R2D2 Malware

To start on this malware expedition, please download image from here .
Once image file is downloaded, lets find out more about it by using volatility imageinfo plugin
C:\volatility>volatility.exe -f 0zapftis.vmem imageinfo
Volatility Foundation Volatility Framework 2.6
INFO : volatility.debug : Determining profile based on KDBG search…
Suggested Profile(s) : WinXPSP2x86, WinXPSP3x86 (Instantiated with WinXPSP2x86)
AS Layer1 : IA32PagedMemoryPae (Kernel AS)
AS Layer2 : FileAddressSpace (C:\volatility\0zapftis.vmem)
PAE type : PAE
DTB : 0x319000L
KDBG : 0x80544ce0L
Number of Processors : 1
Image Type (Service Pack) : 2
KPCR for CPU 0 : 0xffdff000L
KUSER_SHARED_DATA : 0xffdf0000L
Image date and time : 2011–10–10 17:06:54 UTC+0000
Image local date and time : 2011–10–10 13:06:54 -0400
Next, lets take a look at the processes that were running :
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 pslist
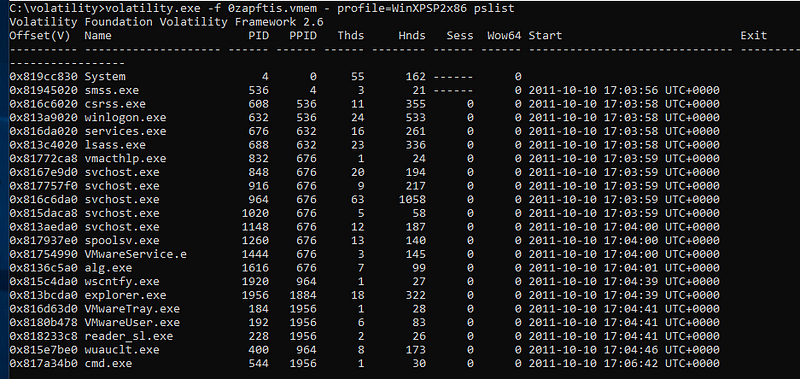
There are 2 processes that standout, first reader_sl.exe and second is cmd.exe.
From our past experience in malware hunting we have come across malwares that have used above processes and we must take closer look at both of them.
Lets use pstree plugin to check hierarchy of processes:
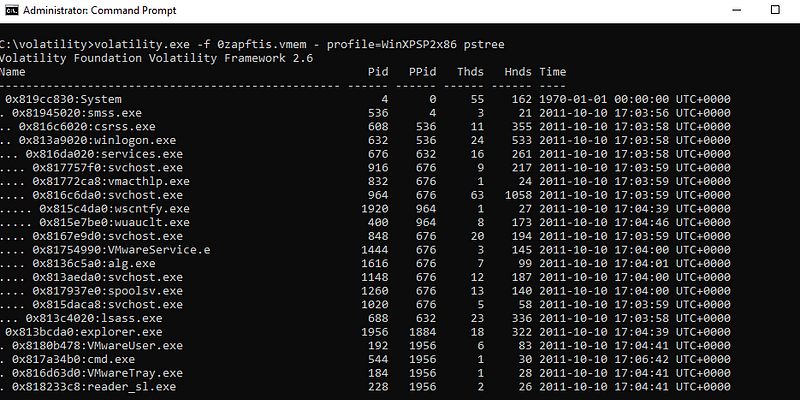
From this, we can see explorer.exe is starting cmd.exe and reader_sl.exe. Prima-facie there is nothing malicious in these. Though before removing these processes from the hook, lets take a look at the commands these were running
To achieve this we will use cmdline plugin
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 cmdline
Volatility Foundation Volatility Framework 2.6
************************************************************************
System pid: 4
************************************************************************
smss.exe pid: 536
Command line : \SystemRoot\System32\smss.exe
************************************************************************
csrss.exe pid: 608
Command line : C:\WINDOWS\system32\csrss.exe ObjectDirectory=\Windows SharedSection=1024,3072,512 Windows=On SubSystemType=Windows ServerDll=basesrv,1 ServerDll=winsrv:UserServerDllInitialization,3 ServerDll=winsrv:ConServerDllInitialization,2 ProfileControl=Off MaxRequestThreads=16
************************************************************************
winlogon.exe pid: 632
Command line : winlogon.exe
************************************************************************
services.exe pid: 676
Command line : C:\WINDOWS\system32\services.exe
************************************************************************
lsass.exe pid: 688
Command line : C:\WINDOWS\system32\lsass.exe
************************************************************************
vmacthlp.exe pid: 832
Command line : “C:\Program Files\VMware\VMware Tools\vmacthlp.exe”
************************************************************************
svchost.exe pid: 848
Command line : C:\WINDOWS\system32\svchost -k DcomLaunch
************************************************************************
svchost.exe pid: 916
Command line : C:\WINDOWS\system32\svchost -k rpcss
************************************************************************
svchost.exe pid: 964
Command line : C:\WINDOWS\System32\svchost.exe -k netsvcs
************************************************************************
svchost.exe pid: 1020
Command line : C:\WINDOWS\system32\svchost.exe -k NetworkService
************************************************************************
svchost.exe pid: 1148
Command line : C:\WINDOWS\system32\svchost.exe -k LocalService
************************************************************************
spoolsv.exe pid: 1260
Command line : C:\WINDOWS\system32\spoolsv.exe
************************************************************************
VMwareService.e pid: 1444
Command line : “C:\Program Files\VMware\VMware Tools\VMwareService.exe”
************************************************************************
alg.exe pid: 1616
Command line : C:\WINDOWS\System32\alg.exe
************************************************************************
wscntfy.exe pid: 1920
Command line : C:\WINDOWS\system32\wscntfy.exe
************************************************************************
explorer.exe pid: 1956
Command line : C:\WINDOWS\Explorer.EXE
************************************************************************
VMwareTray.exe pid: 184
Command line : “C:\Program Files\VMware\VMware Tools\VMwareTray.exe”
************************************************************************
VMwareUser.exe pid: 192
Command line : “C:\Program Files\VMware\VMware Tools\VMwareUser.exe”
************************************************************************
reader_sl.exe pid: 228
Command line : “C:\Program Files\Adobe\Reader 9.0\Reader\Reader_sl.exe”
************************************************************************
wuauclt.exe pid: 400
Command line : “C:\WINDOWS\system32\wuauclt.exe” /RunStoreAsComServer Local\[3c4]SUSDSf6f1f89b8c664547b701fa0a7f1b4cf6
************************************************************************
cmd.exe pid: 544
Command line : “C:\WINDOWS\system32\cmd.exe”
As of now everything looks pretty nice.
Lets use cmdscan plugin to find out last executed commands.
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 cmdscan
Volatility Foundation Volatility Framework 2.6
**************************************************
CommandProcess: csrss.exe Pid: 608
CommandHistory: 0x11132d8 Application: cmd.exe Flags: Allocated, Reset
CommandCount: 2 LastAdded: 1 LastDisplayed: 1
FirstCommand: 0 CommandCountMax: 50
ProcessHandle: 0x4c4
Cmd #0 @ 0x4e1eb8: sc query malwar
Cmd #1 @ 0x11135e8: sc query malware
Looks like csrss.exe is trying to start service named malware
To confirm our suspicion lets see if we can see any connections to remote ips. for this lets execute connscan plugin.
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 connscan
Volatility Foundation Volatility Framework 2.6
Offset(P) Local Address Remote Address Pid
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — -
0x01a25a50 0.0.0.0:1026 172.16.98.1:6666 1956
We can see that process 1956 is making a connection to 172.16.98.1. which looks suspicious.
Lets take a look at sockets plugin
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 sockets
Volatility Foundation Volatility Framework 2.6
Offset(V) PID Port Proto Protocol Address Create Time
— — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — — -
0x8177e3c0 1956 1026 6 TCP 0.0.0.0 2011–10–10 17:04:39 UTC+0000
0x81596a78 688 500 17 UDP 0.0.0.0 2011–10–10 17:04:00 UTC+0000
0x8166a008 964 1029 17 UDP 127.0.0.1 2011–10–10 17:04:42 UTC+0000
0x818ddc08 4 445 6 TCP 0.0.0.0 2011–10–10 17:03:55 UTC+0000
0x818328d8 916 135 6 TCP 0.0.0.0 2011–10–10 17:03:59 UTC+0000
0x81687e98 1616 1025 6 TCP 127.0.0.1 2011–10–10 17:04:01 UTC+0000
0x817517e8 964 123 17 UDP 127.0.0.1 2011–10–10 17:04:00 UTC+0000
0x81753b20 688 0 255 Reserved 0.0.0.0 2011–10–10 17:04:00 UTC+0000
0x8174fe98 1148 1900 17 UDP 127.0.0.1 2011–10–10 17:04:41 UTC+0000
0x81753008 688 4500 17 UDP 0.0.0.0 2011–10–10 17:04:00 UTC+0000
0x816118d8 4 445 17 UDP 0.0.0.0 2011–10–10 17:03:55 UTC+0000
Next lets take a dump of process cmd.exe 544
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 procdump -p 544 — dump-dir .
Volatility Foundation Volatility Framework 2.6
Process(V) ImageBase Name Result
— — — — — — — — — — — — — — — — — — — — — — —
0x817a34b0 0x4ad00000 cmd.exe OK: executable.544.exe
As soon as exe file is created, it is immediately flagged by Anti-Virus, thus confirming our suspicion.
Since our malware is trying to start a service lets take a look at all services by using svcscan
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 svcscan | find “malware”
Offset: 0x6f5440
Order: 97
Start: SERVICE_SYSTEM_START
Process ID: -
Service Name: malware
Display Name: malware2
Service Type: SERVICE_KERNEL_DRIVER
Service State: SERVICE_RUNNING
Binary Path: \Driver\malware
Lets take a look at dlls that are loaded in cmd.exe
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 dlllist -p 544
Volatility Foundation Volatility Framework 2.6
************************************************************************
cmd.exe pid: 544
Command line : “C:\WINDOWS\system32\cmd.exe”
Service Pack 2
Base Size LoadCount Path
— — — — — — — — — — — — — — — — —
0x4ad00000 0x61000 0xffff C:\WINDOWS\system32\cmd.exe
0x7c900000 0xb0000 0xffff C:\WINDOWS\system32\ntdll.dll
0x7c800000 0xf4000 0xffff C:\WINDOWS\system32\kernel32.dll
0x77c10000 0x58000 0xffff C:\WINDOWS\system32\msvcrt.dll
0x77d40000 0x90000 0xffff C:\WINDOWS\system32\USER32.dll
0x77f10000 0x46000 0xffff C:\WINDOWS\system32\GDI32.dll
0x5cb70000 0x26000 0x1 C:\WINDOWS\system32\ShimEng.dll
0x6f880000 0x1ca000 0x1 C:\WINDOWS\AppPatch\AcGenral.DLL
0x77dd0000 0x9b000 0x17 C:\WINDOWS\system32\ADVAPI32.dll
0x77e70000 0x91000 0xb C:\WINDOWS\system32\RPCRT4.dll
0x76b40000 0x2d000 0x2 C:\WINDOWS\system32\WINMM.dll
0x774e0000 0x13c000 0x2 C:\WINDOWS\system32\ole32.dll
0x77120000 0x8c000 0x1 C:\WINDOWS\system32\OLEAUT32.dll
0x77be0000 0x15000 0x1 C:\WINDOWS\system32\MSACM32.dll
0x77c00000 0x8000 0x3 C:\WINDOWS\system32\VERSION.dll
0x7c9c0000 0x814000 0x1 C:\WINDOWS\system32\SHELL32.dll
0x77f60000 0x76000 0x3 C:\WINDOWS\system32\SHLWAPI.dll
0x769c0000 0xb3000 0x1 C:\WINDOWS\system32\USERENV.dll
0x5ad70000 0x38000 0x1 C:\WINDOWS\system32\UxTheme.dll
0x10000000 0x59000 0x1 C:\WINDOWS\system32\mfc42ul.dll
0x71ab0000 0x17000 0x2 C:\WINDOWS\system32\WS2_32.dll
0x71aa0000 0x8000 0x1 C:\WINDOWS\system32\WS2HELP.dll
0x71f60000 0x8000 0x1 C:\WINDOWS\system32\snmpapi.dll
0x773d0000 0x102000 0x1 C:\WINDOWS\WinSxS\x86_Microsoft.Windows.Common-Controls_6595b64144ccf1df_6.0.2600.2180_x-ww_a84f1ff9\comctl32.dll
0x5d090000 0x97000 0x1 C:\WINDOWS\system32\comctl32.dll
0x77b40000 0x22000 0x1 C:\WINDOWS\system32\Apphelp.dll
After going through the list mfc42ul.dll caught my eye. So Istarted by doing a google search for this dll and suspicion was confirmed that this is the malicious dll .
Lets take a look at the modules that were loaded
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 modules
Volatility Foundation Volatility Framework 2.6
Offset(V) Name Base Size File
— — — — — — — — — — — — — — — — — — — — — — — — — — —
0x819fc3a0 ntoskrnl.exe 0x804d7000 0x1f6280 \WINDOWS\system32\ntkrnlpa.exe
0x819fc338 hal.dll 0x806ce000 0x20380 \WINDOWS\system32\hal.dll
0x819fc2d0 kdcom.dll 0xf9e9c000 0x2000 \WINDOWS\system32\KDCOM.DLL
0x819fc260 BOOTVID.dll 0xf9dac000 0x3000 \WINDOWS\system32\BOOTVID.dll
0x819fc1f8 ACPI.sys 0xf986d000 0x2e000 ACPI.sys
0x819fc188 WMILIB.SYS 0xf9e9e000 0x2000 \WINDOWS\system32\DRIVERS\WMILIB.SYS
0x819fc120 pci.sys 0xf985c000 0x11000 pci.sys
0x819fc0b0 isapnp.sys 0xf999c000 0x9000 isapnp.sys
0x819fc040 compbatt.sys 0xf9db0000 0x3000 compbatt.sys
0x819f1008 BATTC.SYS 0xf9db4000 0x4000 \WINDOWS\system32\DRIVERS\BATTC.SYS
0x819f1f98 intelide.sys 0xf9ea0000 0x2000 intelide.sys
0x819f1f28 PCIIDEX.SYS 0xf9c1c000 0x7000 \WINDOWS\system32\DRIVERS\PCIIDEX.SYS
0x819f1eb8 MountMgr.sys 0xf99ac000 0xb000 MountMgr.sys
0x819f1e48 ftdisk.sys 0xf983d000 0x1f000 ftdisk.sys
0x819f1dd8 dmload.sys 0xf9ea2000 0x2000 dmload.sys
0x819f1d70 dmio.sys 0xf9817000 0x26000 dmio.sys
0x819f1d00 PartMgr.sys 0xf9c24000 0x5000 PartMgr.sys
0x819f1c90 VolSnap.sys 0xf99bc000 0xd000 VolSnap.sys
0x819f1c28 atapi.sys 0xf97ff000 0x18000 atapi.sys
0x819f1bb8 vmscsi.sys 0xf9db8000 0x3000 vmscsi.sys
0x819f1b48 SCSIPORT.SYS 0xf97e7000 0x18000 \WINDOWS\system32\drivers\SCSIPORT.SYS
0x819f1ae0 disk.sys 0xf99cc000 0x9000 disk.sys
0x819f1a70 CLASSPNP.SYS 0xf99dc000 0xd000 \WINDOWS\system32\DRIVERS\CLASSPNP.SYS
0x819f1a00 fltMgr.sys 0xf97c8000 0x1f000 fltMgr.sys
0x819f1998 sr.sys 0xf97b6000 0x12000 sr.sys
0x819f1928 KSecDD.sys 0xf979f000 0x17000 KSecDD.sys
0x819f18c0 Ntfs.sys 0xf9712000 0x8d000 Ntfs.sys
0x819f1858 NDIS.sys 0xf96e5000 0x2d000 NDIS.sys
0x819f17f0 Mup.sys 0xf96ca000 0x1b000 Mup.sys
0x819f1780 agp440.sys 0xf99ec000 0xb000 agp440.sys
0x817af440 i8042prt.sys 0xf9a2c000 0xd000 \SystemRoot\system32\DRIVERS\i8042prt.sys
0x8166b688 kbdclass.sys 0xf9c5c000 0x6000 \SystemRoot\system32\DRIVERS\kbdclass.sys
0x8166b398 vmmouse.sys 0xf9ea4000 0x2000 \SystemRoot\system32\DRIVERS\vmmouse.sys
0x81725c68 mouclass.sys 0xf9c64000 0x6000 \SystemRoot\system32\DRIVERS\mouclass.sys
0x815f5f10 parport.sys 0xf9646000 0x14000 \SystemRoot\system32\DRIVERS\parport.sys
0x815f5660 serial.sys 0xf9a3c000 0x10000 \SystemRoot\system32\DRIVERS\serial.sys
0x818e3b70 serenum.sys 0xf9e40000 0x4000 \SystemRoot\system32\DRIVERS\serenum.sys
0x81646f10 fdc.sys 0xf9c6c000 0x7000 \SystemRoot\system32\DRIVERS\fdc.sys
0x81646cc8 imapi.sys 0xf9a4c000 0xb000 \SystemRoot\system32\DRIVERS\imapi.sys
0x81646a70 cdrom.sys 0xf9a5c000 0xd000 \SystemRoot\system32\DRIVERS\cdrom.sys
0x818e3b00 redbook.sys 0xf9a6c000 0xf000 \SystemRoot\system32\DRIVERS\redbook.sys
0x81646500 ks.sys 0xf9623000 0x23000 \SystemRoot\system32\DRIVERS\ks.sys
0x81646808 vmci.sys 0xf9a7c000 0xc000 \SystemRoot\system32\DRIVERS\vmci.sys
0x81646a00 vmx_svga.sys 0xf9a8c000 0xe000 \SystemRoot\system32\DRIVERS\vmx_svga.sys
0x8163dbd8 VIDEOPRT.SYS 0xf960f000 0x14000 \SystemRoot\system32\DRIVERS\VIDEOPRT.SYS
0x8163dcd8 usbuhci.sys 0xf9c74000 0x5000 \SystemRoot\system32\DRIVERS\usbuhci.sys
0x814d0de0 USBPORT.SYS 0xf95ec000 0x23000 \SystemRoot\system32\DRIVERS\USBPORT.SYS
0x81725df8 vmxnet.sys 0xf9c7c000 0x8000 \SystemRoot\system32\DRIVERS\vmxnet.sys
0x814cf138 es1371mp.sys 0xf9a9c000 0xa000 \SystemRoot\system32\drivers\es1371mp.sys
0x8163d128 portcls.sys 0xf95c8000 0x24000 \SystemRoot\system32\drivers\portcls.sys
0x8160bfa0 drmk.sys 0xf9aac000 0xf000 \SystemRoot\system32\drivers\drmk.sys
0x814d0bc8 usbehci.sys 0xf9c84000 0x7000 \SystemRoot\system32\DRIVERS\usbehci.sys
0x8160bf30 CmBatt.sys 0xf9e48000 0x4000 \SystemRoot\system32\DRIVERS\CmBatt.sys
0x8160bda0 intelppm.sys 0xf9abc000 0x9000 \SystemRoot\system32\DRIVERS\intelppm.sys
0x8160bb90 audstub.sys 0xfa0ee000 0x1000 \SystemRoot\system32\DRIVERS\audstub.sys
0x8192a418 rasl2tp.sys 0xf9acc000 0xd000 \SystemRoot\system32\DRIVERS\rasl2tp.sys
0x8192a2b0 ndistapi.sys 0xf9e4c000 0x3000 \SystemRoot\system32\DRIVERS\ndistapi.sys
0x814d08c0 ndiswan.sys 0xf95b1000 0x17000 \SystemRoot\system32\DRIVERS\ndiswan.sys
0x8192a240 raspppoe.sys 0xf9adc000 0xb000 \SystemRoot\system32\DRIVERS\raspppoe.sys
0x8192a1d0 raspptp.sys 0xf9aec000 0xc000 \SystemRoot\system32\DRIVERS\raspptp.sys
0x8160b1a0 TDI.SYS 0xf9c8c000 0x5000 \SystemRoot\system32\DRIVERS\TDI.SYS
0x81929a58 psched.sys 0xf94d8000 0x11000 \SystemRoot\system32\DRIVERS\psched.sys
0x8148d908 msgpc.sys 0xf9afc000 0x9000 \SystemRoot\system32\DRIVERS\msgpc.sys
0x81652398 ptilink.sys 0xf9c94000 0x5000 \SystemRoot\system32\DRIVERS\ptilink.sys
0x816736c0 raspti.sys 0xf9c9c000 0x5000 \SystemRoot\system32\DRIVERS\raspti.sys
0x8148d0d0 rdpdr.sys 0xf94a7000 0x31000 \SystemRoot\system32\DRIVERS\rdpdr.sys
0x8164d138 termdd.sys 0xf9b0c000 0xa000 \SystemRoot\system32\DRIVERS\termdd.sys
0x81941e78 swenum.sys 0xf9ea6000 0x2000 \SystemRoot\system32\DRIVERS\swenum.sys
0x81708d20 update.sys 0xf9473000 0x34000 \SystemRoot\system32\DRIVERS\update.sys
0x8148d230 mssmbios.sys 0xf9e6c000 0x4000 \SystemRoot\system32\DRIVERS\mssmbios.sys
0x81708150 NDProxy.SYS 0xf9b1c000 0xa000 \SystemRoot\System32\Drivers\NDProxy.SYS
0x81708dc0 flpydisk.sys 0xf9ca4000 0x5000 \SystemRoot\system32\DRIVERS\flpydisk.sys
0x818e5f70 usbhub.sys 0xf9b3c000 0xf000 \SystemRoot\system32\DRIVERS\usbhub.sys
0x8189ec78 USBD.SYS 0xf9ea8000 0x2000 \SystemRoot\system32\DRIVERS\USBD.SYS
0x818e5958 gameenum.sys 0xf9e94000 0x3000 \SystemRoot\system32\DRIVERS\gameenum.sys
0x817a8668 Fs_Rec.SYS 0xf9eaa000 0x2000 \SystemRoot\System32\Drivers\Fs_Rec.SYS
0x8189e258 Null.SYS 0xf9fcf000 0x1000 \SystemRoot\System32\Drivers\Null.SYS
0x8189e058 Beep.SYS 0xf9eac000 0x2000 \SystemRoot\System32\Drivers\Beep.SYS
0x8190be80 vga.sys 0xf9cb4000 0x6000 \SystemRoot\System32\drivers\vga.sys
0x8190bc80 mnmdd.SYS 0xf9eae000 0x2000 \SystemRoot\System32\Drivers\mnmdd.SYS
0x8161a090 RDPCDD.sys 0xf9eb0000 0x2000 \SystemRoot\System32\DRIVERS\RDPCDD.sys
0x8190b868 Msfs.SYS 0xf9cbc000 0x5000 \SystemRoot\System32\Drivers\Msfs.SYS
0x8190b638 Npfs.SYS 0xf9cc4000 0x8000 \SystemRoot\System32\Drivers\Npfs.SYS
0x817a5ba8 rasacd.sys 0xf9689000 0x3000 \SystemRoot\system32\DRIVERS\rasacd.sys
0x8190b260 ipsec.sys 0xf1218000 0x13000 \SystemRoot\system32\DRIVERS\ipsec.sys
0x8180cfa0 tcpip.sys 0xf11c0000 0x58000 \SystemRoot\system32\DRIVERS\tcpip.sys
0x8180ccb0 netbt.sys 0xf1198000 0x28000 \SystemRoot\system32\DRIVERS\netbt.sys
0x816143a0 ws2ifsl.sys 0xf9685000 0x3000 \SystemRoot\System32\drivers\ws2ifsl.sys
0x8180c7a8 afd.sys 0xf114e000 0x22000 \SystemRoot\System32\drivers\afd.sys
0x81480630 netbios.sys 0xf9b4c000 0x9000 \SystemRoot\system32\DRIVERS\netbios.sys
0x816ff3a0 vmhgfs.sys 0xf1132000 0x1c000 \SystemRoot\System32\DRIVERS\vmhgfs.sys
0x817eba60 rdbss.sys 0xf1106000 0x2c000 \SystemRoot\system32\DRIVERS\rdbss.sys
0x81921300 mrxsmb.sys 0xf1097000 0x6f000 \SystemRoot\system32\DRIVERS\mrxsmb.sys
0x8177f228 winsys32.sys 0xf9eb4000 0x2000 \??\C:\WINDOWS\system32\drivers\winsys32.sys
0x817eb2c0 Fips.SYS 0xf9b6c000 0x9000 \SystemRoot\System32\Drivers\Fips.SYS
0x817eb0f0 ipnat.sys 0xf1076000 0x21000 \SystemRoot\system32\DRIVERS\ipnat.sys
0x815bb120 wanarp.sys 0xf9b7c000 0x9000 \SystemRoot\system32\DRIVERS\wanarp.sys
0x817ae590 Cdfs.SYS 0xf9b9c000 0x10000 \SystemRoot\System32\Drivers\Cdfs.SYS
0x817980d8 usbccgp.sys 0xf9cd4000 0x8000 \SystemRoot\system32\DRIVERS\usbccgp.sys
0x818a21c8 hidusb.sys 0xf959d000 0x3000 \SystemRoot\system32\DRIVERS\hidusb.sys
0x819264c8 HIDCLASS.SYS 0xf9bac000 0x9000 \SystemRoot\system32\DRIVERS\HIDCLASS.SYS
0x81925280 HIDPARSE.SYS 0xf9cdc000 0x7000 \SystemRoot\system32\DRIVERS\HIDPARSE.SYS
0x8180a0e8 mouhid.sys 0xf9599000 0x3000 \SystemRoot\system32\DRIVERS\mouhid.sys
0x817220e0 dump_scsiport.sys 0xf9595000 0x4000 \SystemRoot\System32\Drivers\dump_diskdump.sys
0x8171fa20 dump_vmscsi.sys 0xf9591000 0x3000 \SystemRoot\System32\Drivers\dump_vmscsi.sys
0x813d0918 win32k.sys 0xbf800000 0x1c1000 \SystemRoot\System32\win32k.sys
0x81642890 watchdog.sys 0xf9ce4000 0x5000 \SystemRoot\System32\watchdog.sys
0x818a3f60 Dxapi.sys 0xf946f000 0x3000 \SystemRoot\System32\drivers\Dxapi.sys
0x8189b008 dxg.sys 0xbf9c1000 0x12000 \SystemRoot\System32\drivers\dxg.sys
0x819474e8 dxgthk.sys 0xfa00f000 0x1000 \SystemRoot\System32\drivers\dxgthk.sys
0x815b6310 vmx_fb.dll 0xbf9d3000 0x29000 \SystemRoot\System32\vmx_fb.dll
0x8183c260 ndisuio.sys 0xf0eb2000 0x4000 \SystemRoot\system32\DRIVERS\ndisuio.sys
0x8181b898 mrxdav.sys 0xf0cd9000 0x2d000 \SystemRoot\system32\DRIVERS\mrxdav.sys
0x815ba4e8 ParVdm.SYS 0xf9ec6000 0x2000 \SystemRoot\System32\Drivers\ParVdm.SYS
0x81796b38 vmmemctl.sys 0xf9ec8000 0x2000 \??\C:\Program Files\VMware\VMware Tools\Drivers\memctl\vmmemctl.sys
0x81720b58 srv.sys 0xf0c5e000 0x53000 \SystemRoot\system32\DRIVERS\srv.sys
0x8187ea58 wdmaud.sys 0xf0a41000 0x15000 \SystemRoot\system32\drivers\wdmaud.sys
0x816cb5b8 sysaudio.sys 0xf0ad6000 0xf000 \SystemRoot\system32\drivers\sysaudio.sys
0x8181af08 kmixer.sys 0xf09cc000 0x2a000 \SystemRoot\system32\drivers\kmixer.sys
0x81783008 HTTP.sys 0xf07f3000 0x41000 \SystemRoot\System32\Drivers\HTTP.sys
Immediately we can see that driver winsys32.sys is getting loaded from C:\windows, confirming our suspicion
0x8177f228 winsys32.sys 0xf9eb4000 0x2000 \??\C:\WINDOWS\system32\drivers\winsys32.sys
Lets take a dump of memory and analyze it further by using memdmp plugin
C:\volatility>volatility.exe -f 0zapftis.vmem — profile=WinXPSP2x86 memdump -p 544 — dump-dir .
Volatility Foundation Volatility Framework 2.6
************************************************************************
Writing cmd.exe [ 544] to 544.dmp
Lets take a look at this dump file and on running strings against it we can find below information
skype.exe seamonkey.exe navigator.exe opera.exe iexplore.exe firefox.exe %d.%d.%d.%d I“”–”(“ƒh(¨õ
¹”E“¼×ó“õ2“ DUMMY!DUMMY SYS!ICP!94062 C3PO-r2d2-POE %s %d CONNECT %s:%d HTTP/1.0
Thus confirming we have successfully hunted R2D2 malware.

what is the password for the rar file?