This is a part 2 of challenge posted on cyberdefenders.org and you can find it here.
For part 1, please refer to my previous post
Q7:What is the server certificate public key that was used in TLS session: da4a0000342e4b73459d7360b4bea971cc303ac18d29b99067e46d16cc07f4ff?
To answer this question, first lets filter the traffic by TLS protocol and navigate to any Server Hello packet as shown below :
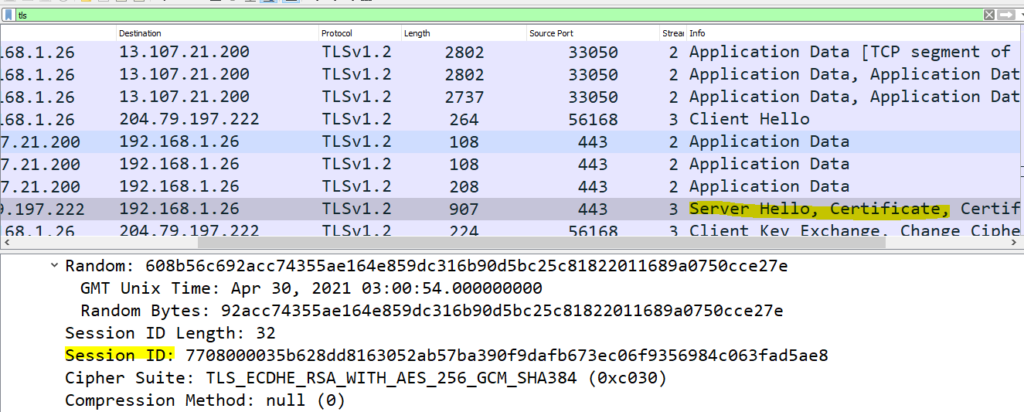
In the snippet above ,you will notice session id of the selected packet, now right click on the Session Id and apply it as filter as shown below
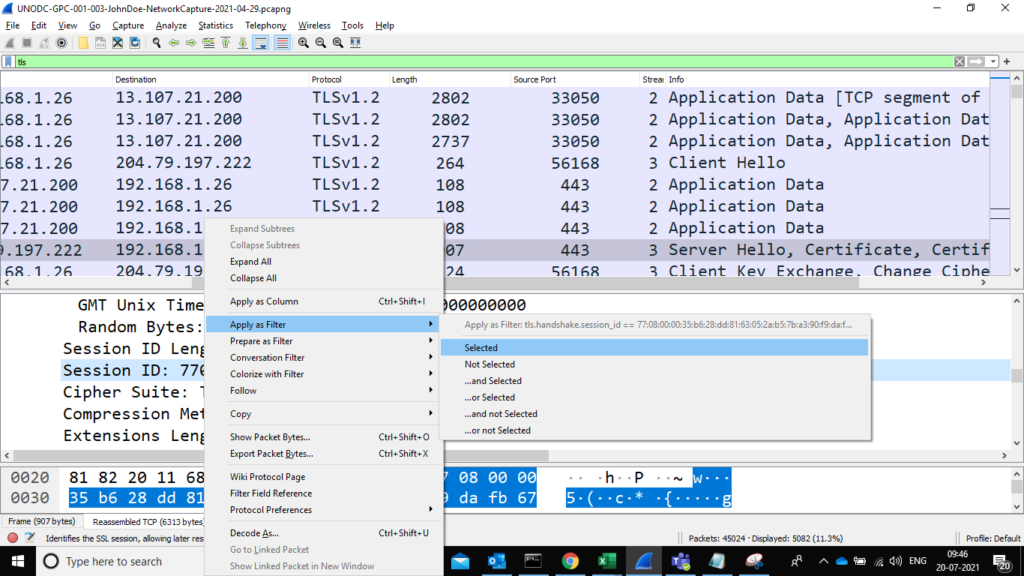
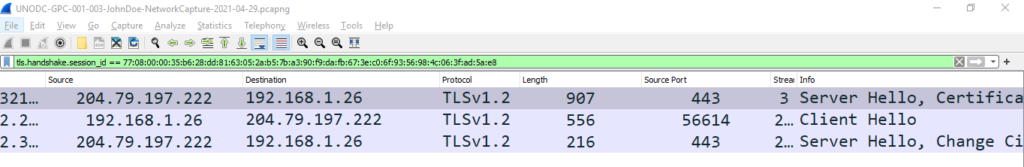
Now we have a filter that can filter packets with TLS session ids and from here we can replace the selected session id with the session id ‘da4a0000342e4b73459d7360b4bea971cc303ac18d29b99067e46d16cc07f4ff’ given in the question but this will consume time and effort. To fasten the process, I used slice operator as below.
tls.handshake.session_id[0:1]== daThis will search TLS Session Ids starting with “da” and will show the results as shown in snippet below.
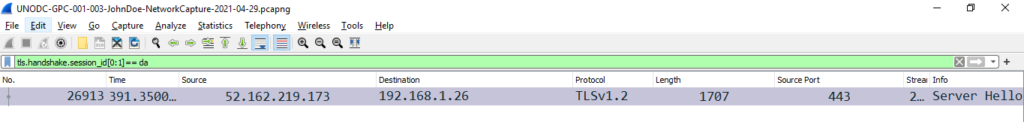
Now all we need to do is scroll down and search for public key and answer the question.
Q8: What is the first TLS 1.3 client random that was used to establish a connection with protonmail.com?
To answer this question we need to find the IP of protonmail.com server. For this we can use below filter
dns.qry.name == "protonmail.com"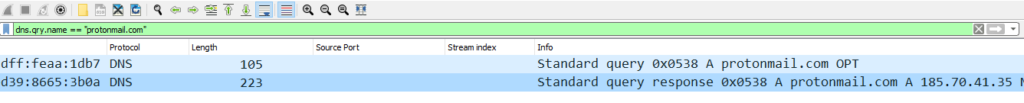
From the snippet we can see that 185.70.41.35 is the ip of protonmail.com. Now we need to find out the first TLS 1.3 client random. To do this filter our the traffic with above IP and TLS protocol with below filter
ip.addr==185.70.41.35 and tls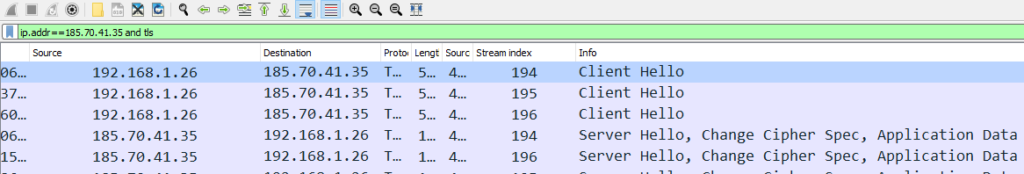
Now all we need to do is copy the Random number from first line.
Q9:What country is the MAC address of the FTP server registered in? (two words, one space in between)
To answer this question, we need to find the MAC address of the ftp server. To do this filter the traffic with ftp and select the line with ftp server as shown below
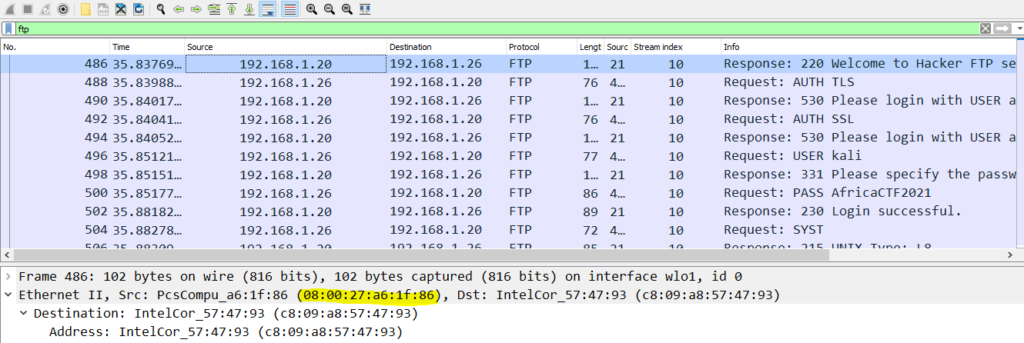
From above snippet we can get the MAC address of the FTP server. For ease I have highlighted the same. Now to find out the location use any internet site for finding country code .I used https://macaddress.io/ to answer the question.
Q10: What time was a non-standard folder created on the FTP server on the 20th of April? (hh:mm)
To answer this question I was planning to filter ftp-data traffic and then based on ftp commands add a new column or add it as filter. Luckily the answer was in the very first line of ftp-data traffic.
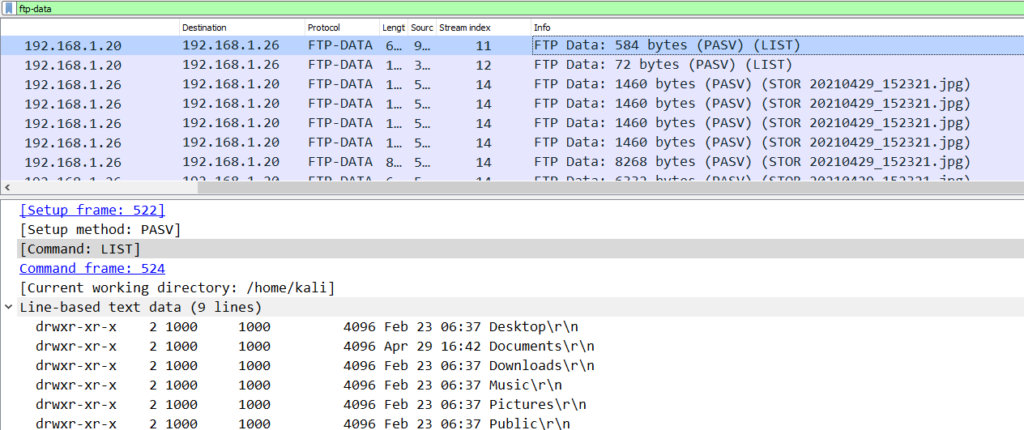
From the snippet we can easily find the answer in Line -Based text data
Q11: What domain was the user connected to in packet 27300?
To find out the answer we need to go to the packet number mentioned in the question and from there get the IP address of the server

IP address is 172.67.162.206.
Now navigate to statistics-> Resolved Address and you can easily get the answer
Conclusion
To conclude we used some standard and some on-standard filters to answer the questions. List of filters is documented below :
1. ftp-data
2. ftp
3. tls.handshake.session_id[0:1]== da
4. dns.qry.name == "protonmail.com"
5. ip.addr==185.70.41.35 and tlsOverall I am satisfied with the difficulty level of the challenge and it is definitely worth time and effort
