ROOT-Me.org Network FTP-authentication Challenges

In this challenge a pcap file is provided and we have to find the user password
To start with download the pcap file and open it in Wireshark.
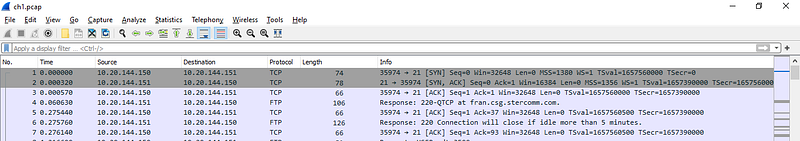
In the first three lines we can see 2 way TCP Handshake (Syn, Ack, Syn-Ack) between source and destination server.
Next we can see ftp connection to fran.csg.stercomm.com. Lets right click on FTP stream and select ‘follow TCP Stream’ and we will get tcp stream
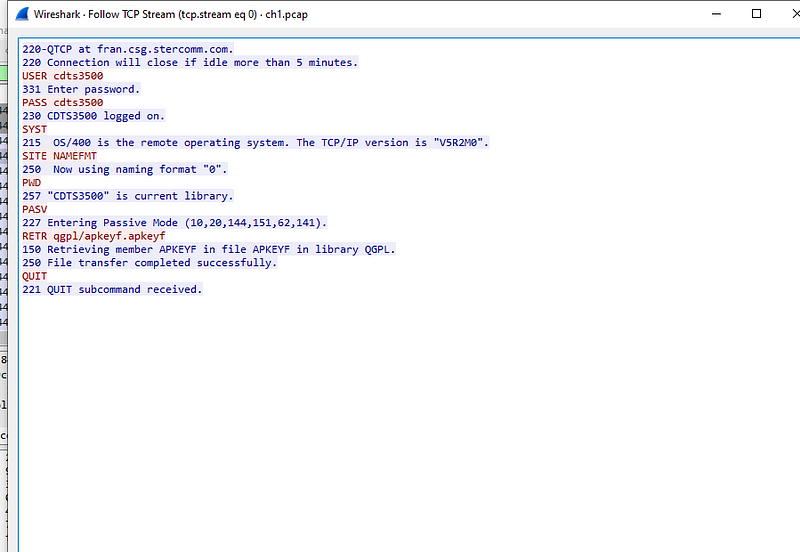
One glance and we can see user and password in clear text.
Conclusion we should avoid sending data over ftp and should rather user sftp or other safe protocols
Challenge 2 : TELNET — authentication
Challenge is to find user password in this telnet capture
In this challenge we have a pcap file having Telnet and TCP protocols.
After opening the file in wireshark, right click on the TELNET protocol and do follow TCP stream
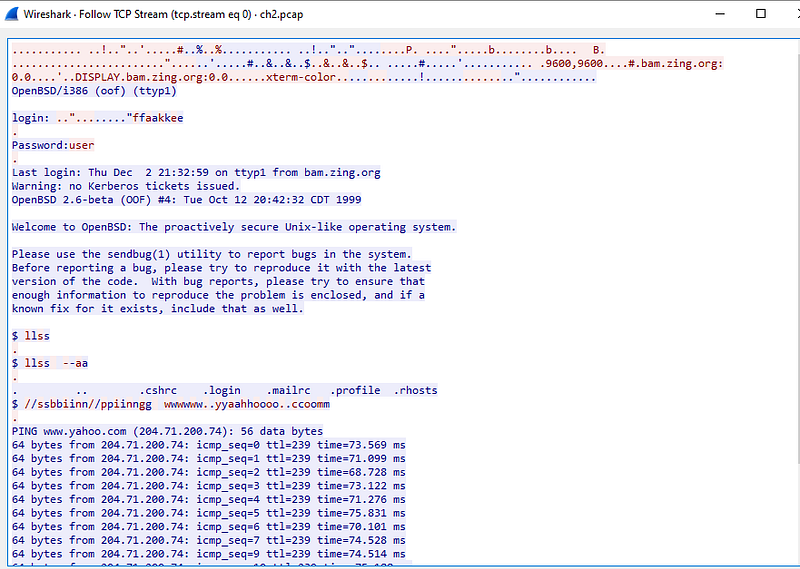
From the screenshot we can see that login credentials are in clear text. Now, input the password to clear this challenge
Challenge Twitter authentication
In this challenge, we have a twitter session authentication capture and need to find user password.
After downloading the pcap file and opening it in Wireshark, we can see that is consists of only 1 Http request
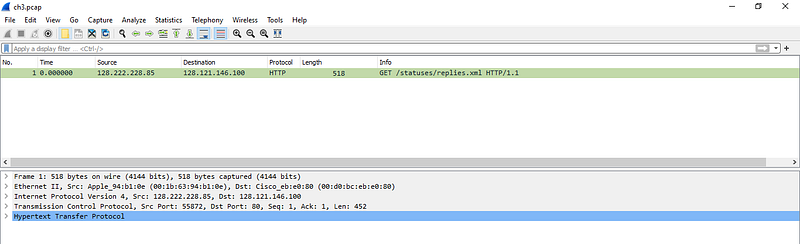
We are aware that http send request/response in clear text. So lets take a closer look at the HTTP data by clicking and enlarging Hypertext Transfer Protocol in middle pane of wireshark
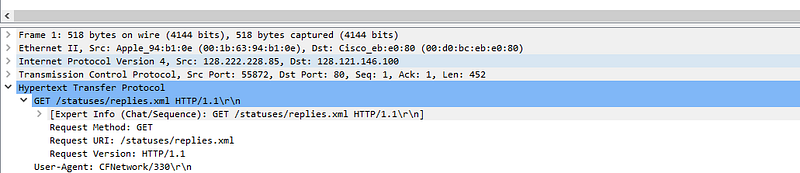
In the above screenshot we can see Get request . On scrolling further, under authorization Header we can see user password in clear text

