Category: Forensic
The challenge involves analyzing .pcap file having multiple protocols.
In this particular challenge we need to analyze SMB protocol and find the missing flag.

Prerequisites:
- Knowledge of a network capture analyzing tool.
- Knowledge of the group policy.
- Knowledge of Python
You can find the challenge at below link :
https://www.root-me.org/en/Challenges/Forensic/Active-Directory-GPO
Statement
During a security audit, the network traffic during the boot sequence of a workstation connected to a Active Directory was recorded. Analyze this capture and find the administrator’s password.
First lets download the ch12.pcap file from the challenge and open it in Wireshark
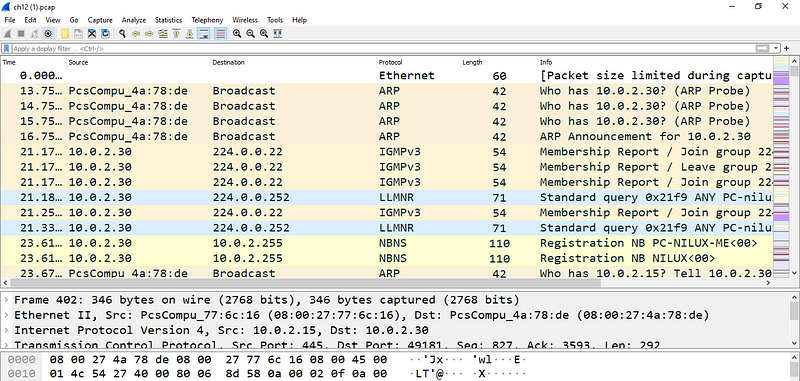
Now, before taking a deep dive into the packet capture lets take a high level view of different protocols. To do this navigate to Statistics →Protocol Hierarchy
And you will see below window, showing different protocols
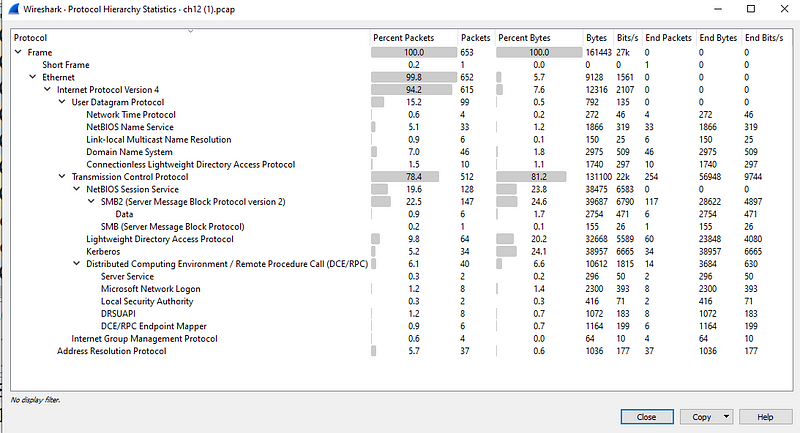
Lets, take a closer look at different protocols and immediately SMB2 caught my eye in the list.
What is SMB
Wikipedia states :
In computer networking, Server Message Block (SMB), one version of which was also known as Common Internet File System (CIFS /sɪfs/),[1][2] is a communication protocol[3] for providing shared access to files, printers, and serial ports between nodes on a network. It also provides an authenticated inter-process communication mechanism.
Lets, filter the data with SMB2 protocol. To do this, just type smb2 in the filter bar and we will only see traffic using SMB2 protocol
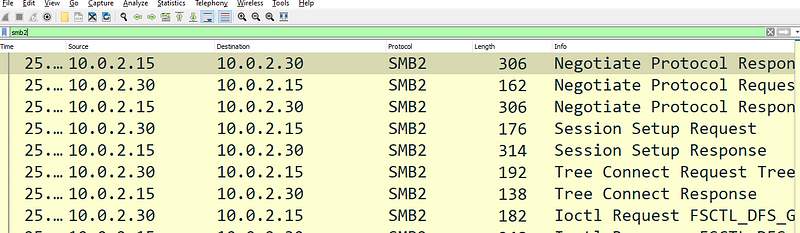
Once we have filtered by SMB2 protocol, lets take a closer look.
- There are 2 stream indexes numbered 14 and 24.
- Stream index 14 is trying to setup session and then terminates
- Stream index 24 contains more data as compared to 14
Lets follow stream index 24, to do so, right click — ->Follow TCP stream
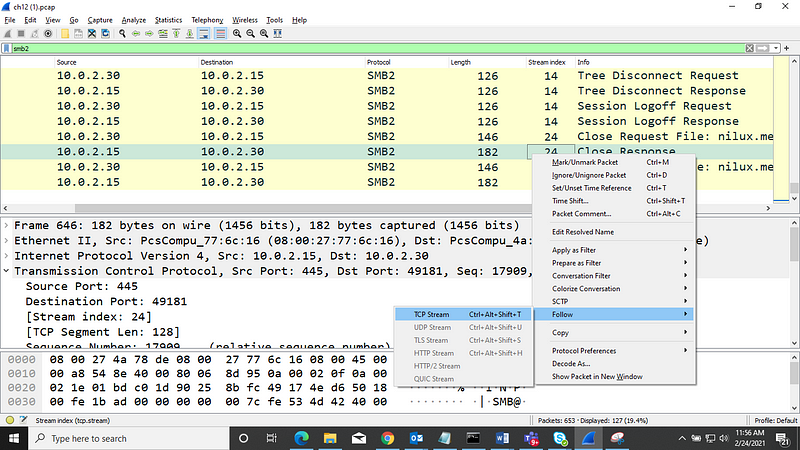
and we can see all request and response in red and blue respectively
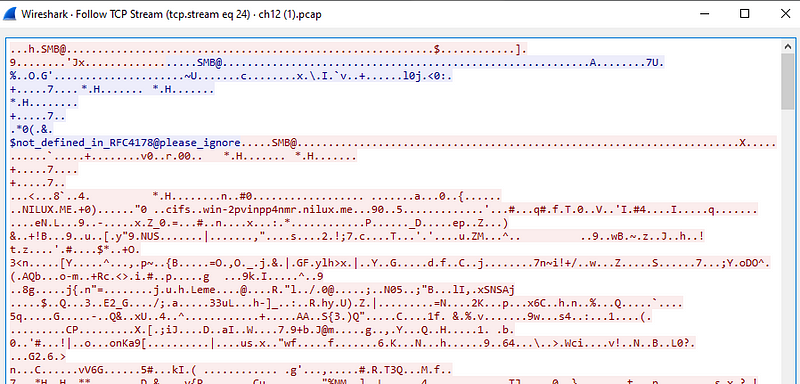
Scrolling through the stream we come across a xml file in clear text :
<?xml version=”1.0" encoding=”utf-8"?>
<Groups clsid=”{3125E937-EB16–4b4c-9934–544FC6D24D26}”><User clsid=”{DF5F1855–51E5–4d24–8B1A-D9BDE98BA1D1}” name=”Helpdesk” image=”2" changed=”2015–05–06 05:50:08" uid=”{43F9FF29-C120–48B6–8333–9402C927BE09}”><Properties action=”U” newName=”” fullName=”” description=”” cpassword=”PsmtscOuXqUMW6KQzJR8RWxCuVNmBvRaDElCKH+FU+w” changeLogon=”1" noChange=”0" neverExpires=”0" acctDisabled=”0" userName=”Helpdesk”/></User><User clsid=”{DF5F1855–51E5–4d24–8B1A-D9BDE98BA1D1}” name=”Administrateur” image=”2" changed=”2015–05–05 14:19:53" uid=”{5E34317F-8726–4F7C-BF8B-91B2E52FB3F7}” userContext=”0" removePolicy=”0"><Properties action=”U” newName=”” fullName=”Admin Local” description=”” cpassword=”LjFWQMzS3GWDeav7+0Q0oSoOM43VwD30YZDVaItj8e0" changeLogon=”0" noChange=”0" neverExpires=”1" acctDisabled=”0" subAuthority=”” userName=”Administrateur”/></User>
</Groups>
If we look at data above we can see :
name=”Administrateur”
cpassword=”LjFWQMzS3GWDeav7+0Q0oSoOM43VwD30YZDVaItj8e0″
As you can see we have password of Administrator but it is encrypted. Now to complete the challenge we have to break the password.
Decrypting Password
Find AES Key
To decrypt AES encrypted password we need the key that was used for encrypting the password.
To find the key that MS is using for encrypting passwords, lets start with searching for the key on google. After searching for few minutes, found the key at :
All passwords are encrypted using a derived Advanced Encryption Standard (AES) key.
The 32-byte AES key is as follows:
4e 99 06 e8 fc b6 6c c9 fa f4 93 10 62 0f fe e8 f4 96 e8 06 cc 05 79 90 20 9b 09 a4 33 b6 6c 1b
Now, we have the key that was used for encrypting password and next step is to find a way to decrypt AES password.
Decrypting AES password
Since I am not very familiar with crypto, I decided to use the python code given at https://github.com/MartinIngesen/gpocrack/blob/master/gpocrack.py
Unfortunately, the given code did not work for me and after taking closer look and making some changes it finally worked
!pip install pycrypto from Crypto.Cipher import AES import base64
cpassword="LjFWQMzS3GWDeav7+0Q0oSoOM43VwD30YZDVaItj8e0="
decoded_password = base64.b64decode(cpassword)
key = b'\x4e\x99\x06\xe8\xfc\xb6\x6c\xc9\xfa\xf4\x93\x10\x62\x0f\xfe\xe8\xf4\x96\xe8\x06\xcc\x05\x79\x90\x20\x9b\x09\xa4\x33\xb6\x6c\x1b'
decryption_suite = AES.new(key, AES.MODE_CBC, '\x00'*16)
plain_text = decryption_suite.decrypt(decoded_password)
print("Password is: {}".format(plain_text.strip()))
password_list = (plain_text.decode().split('\x00')) # removing null bytes
password = ''.join(str(i) for i in password) # list to string
print(password)
References
3. Wikipedia

I know this if off topic but I’m looking into starting my own weblog and
was wondering what all is required to get setup?
I’m assuming having a blog like yours would cost a pretty penny?
I’m not very internet smart so I’m not 100% certain.
Any recommendations or advice would be greatly appreciated.
Thanks
Hi, if you want can help you setup wordpress blog.