This is a brief writeup of challenge posted on cyberdefenders.org and you can find it here.
Challenge
As an analyst working for a security service provider, you have been tasked with analyzing a packet capture for a customer’s employee whose network activity has been monitored for a while -possible insider
As part of this challenge a pcap file is provided and based on it you have to answer 11 questions which get progressively difficult as you move ahead. In this article I will refrain from posting any answers but after reading you can get decent idea of the approach. So before proceeding ahead please make sure you have tried your level best.
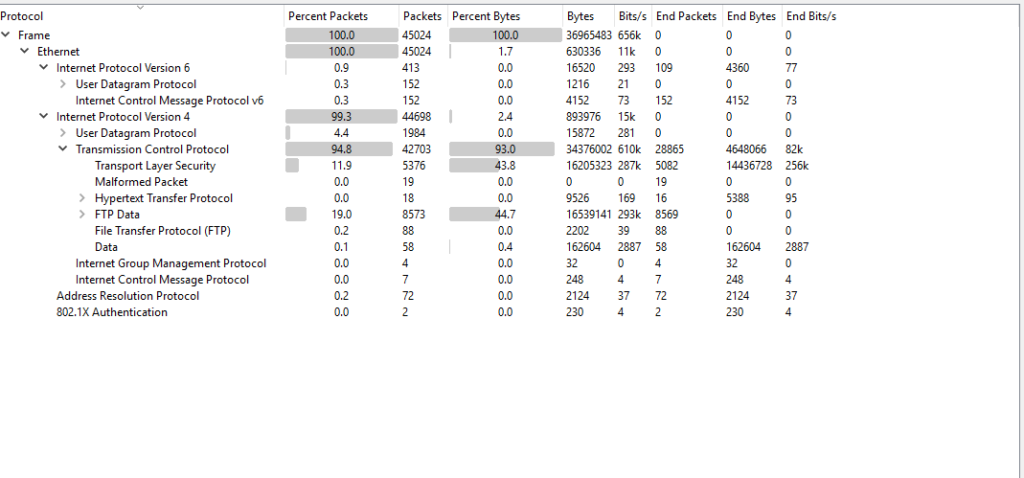
Before jumping on to the questions lets quickly review the pcap file in wireshark. Once you have opened the file in wireshark, navigate to Statistics——->Protocol Hierarchy and you will see below window. From this you will get a decent idea of different protocols that were captured like in our case we can see FTP,FTP-Data, HTTP, TLS etc. After briefly analyzing this lets jump to the questions posted in the challenge.
Question 1 : What is the FTP password?
I think this was the easiest question and if you are used to DFIR challenges, you must have encountered this before.
To solve this we need to filter out the captured FTP traffic . To do this, we will use FTP filter as shown below in the screenshot and this will filter out all other protocols
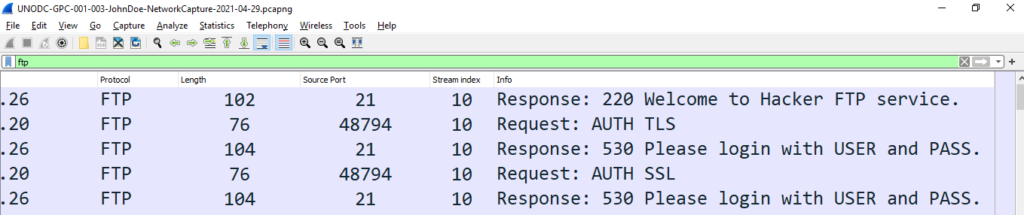
As we know that in FTP protocol data is not encrypted and from the screenshot we can clearly see the messages in clear text. Further analysis will reveal the answer to question 1
Question 2: What is the IPv6 address of the DNS server used by 192.168.1.26?
To solve this question lets again filter the traffic with DNS protocol. To do this just type ‘DNS’ in the filter bar and you will see all the DNS traffic as shown below:
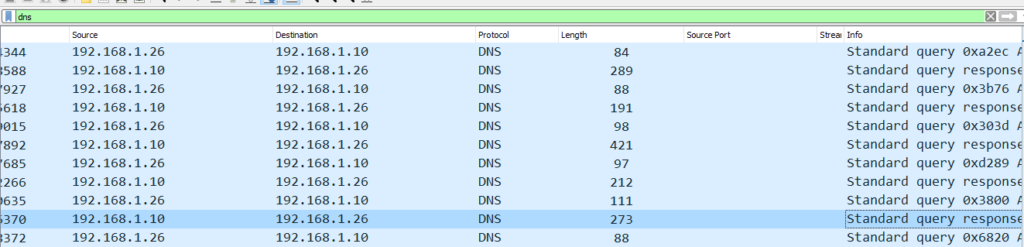
From the above snippet we can see that 192.168.1.26 is sending a DNS query to 192.168.1.10 and then in the next line receiving response from 192.168.1.10. From this we can conclude that ipv4 address of DNS server is 192.168.1.10.
On scrolling down further, you will see IPV6 addresses of servers and extrapolating the above logic i.e. DNS server receives queries from other servers and then responds to other queries in the same fashion as shown in snippet above, you can easily figure out the ipv6 address of the DNS server.
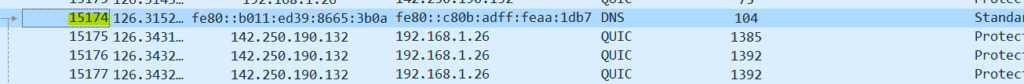
Question 3:What domain is the user looking up in packet 15174?
Here we are given a packet number and the easiest way to reach a packet in Wireshark is to navigate to Go—->Go to Packet or simply user CTRL+G, this will open a small window where you can enter the packet number as shown below.
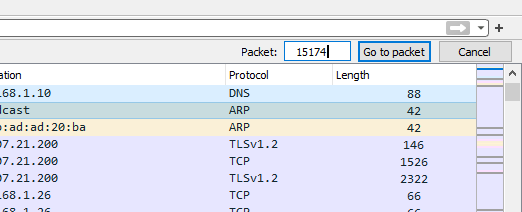
ON pressing enter or Go To packet button you will be taken directly to the line with entered packet number or in our case directly to the answer
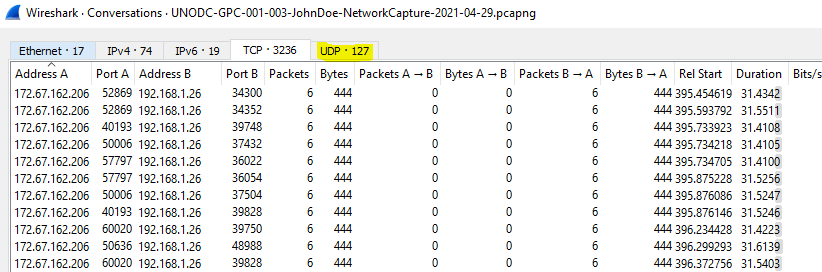
Question 4: How many UDP packets were sent from 192.168.1.26 to 24.39.217.246?
The easiest way to answer this question is to navigate to Statistics——>Conversations as shown below
Once you reach the below window, select UDP tab and you should have the answer:
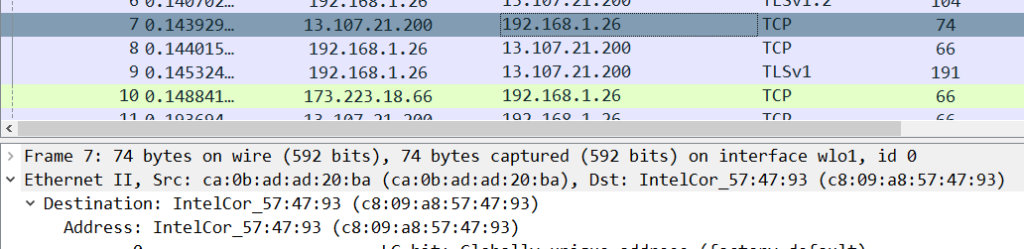
Question 5: What is the MAC address of the system being monitored?
By now you would have realized that 92.168.1.26 is the server ip that is under monitoring. click on any line containing this IP and under Ethernet you will find the answer
Q6: What was the camera model name used to take picture 20210429_152157.jpg ?
To solve this I started with navigating to File—>Export Object—>HTTP
After selecting HTTP below window opened but here could not see the mentioned jpg file in the list
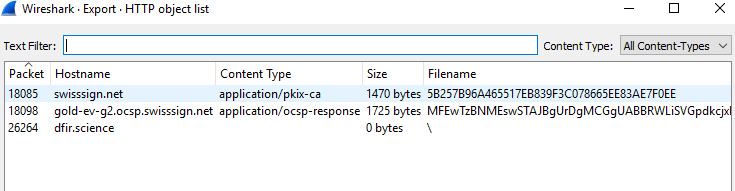
Similarly, I tried all the other options DICOM, IMF, SMB and TFTP but no luck. Immediately my mind went to the list of protocols at the start of the challenge and on referring back I saw FTP Data protocol in the list and decided to filter traffic by it.
To filter by ftp-data protocol just type ftp-data in the filter bar as shown below:
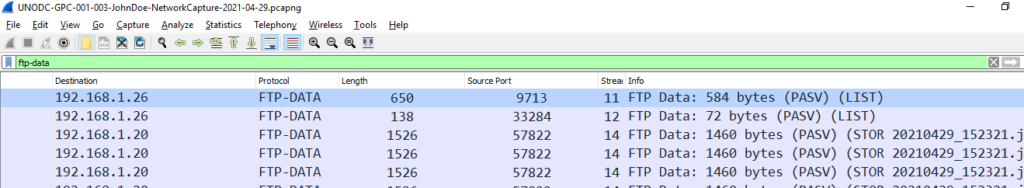
We can see that immediately the file name pops up in the info tab. Now that I have located the jpg file , I needed a way to download it. so I decided to follow the complete stream 14 by doing right click and then selecting Follow——> TCP stream
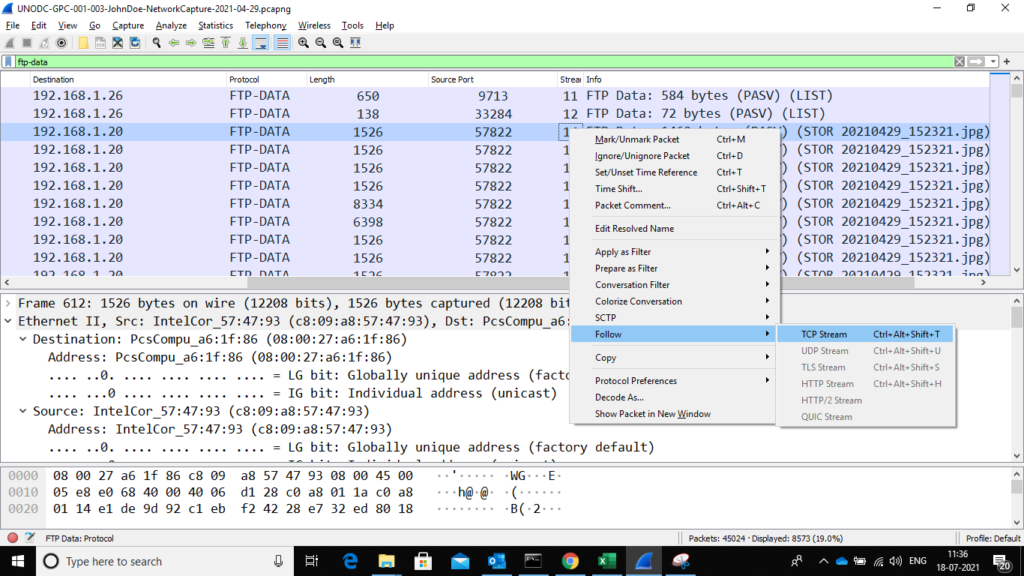
Once TCP stream is clicked it will take you to below window:
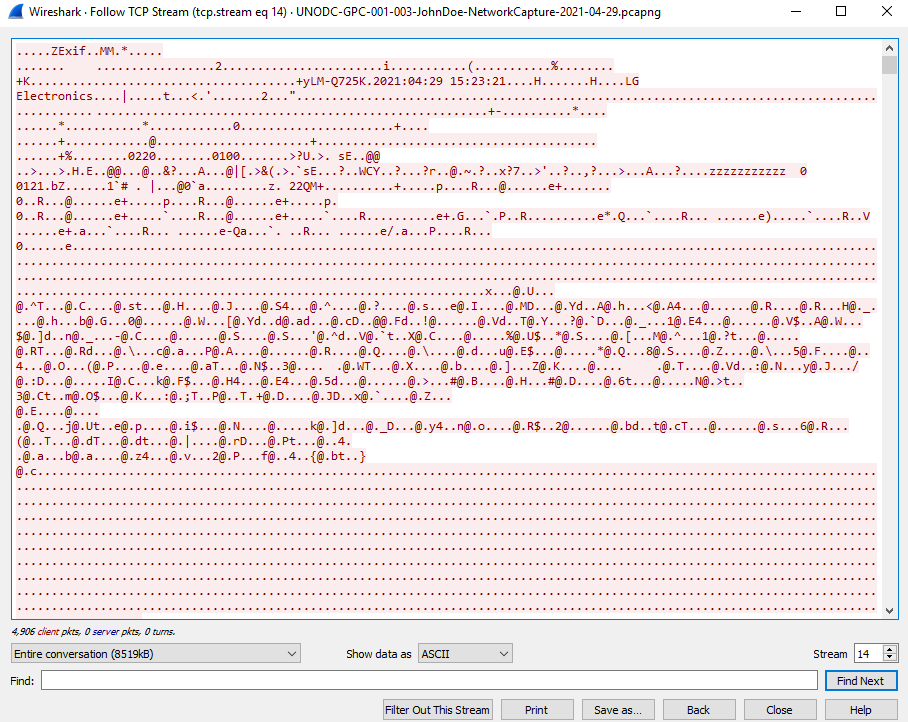
Here we can see the data in ASCII format, now click on Show data Drop down and select Raw data as shown in below window
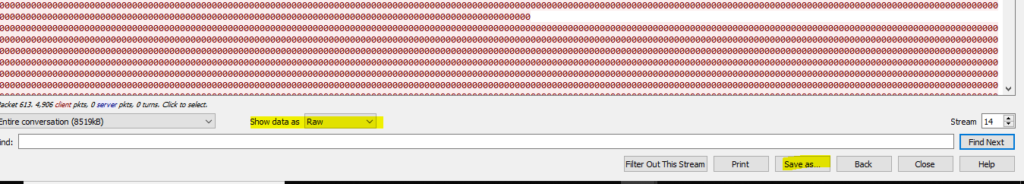
Once the data loading is complete click in save as and save the file in .jpg format. Now that we have successfully extracted the jpg file, it is time to extract the meta-data from it and answer the question. I used https://brandfolder.com/ to extract the meta-data from the image and answer the question
Conclusion
I will conclude the Part 1 of the series here. You can see that as we are progressing the difficulty of questions is increasing and so is the fun. In all this was a very balanced challenge which not only brushed up my Wireshark knowledge but also made me think and google for lots of stuff. Please continue watching this space for part 2.
